The year 2024 has seen a significant rise in cyber attacks, highlighting the urgent need for robust cybersecurity measures across all sectors. One of the most notable incidents involved Bank of America, which suffered a data breach affecting 57,028 individuals due to a cyberattack on Infosys McCamish Systems. This breach exposed sensitive information such as names, social security numbers, and account details, emphasizing the cascading risks associated with interconnected service ecosystems (Techopedia).
In another major incident, McLaren Health Care in Michigan reported a data breach that compromised the personal information of approximately 2.2 million patients. This breach, which went undetected for nearly a month, exposed critical data including full names, social security numbers, and personal health information. The affected individuals are now offered credit monitoring and identity protection services to mitigate the impact of the breach (Firewall Times).
Furthermore, the cyber landscape saw a sophisticated attack on the Indian Council of Medical Research (ICMR), affecting around 815 million individuals. This breach exposed sensitive data related to COVID-19 testing and highlighted the vulnerabilities in health data management systems. Such large-scale breaches underscore the importance of stringent cybersecurity measures and proactive threat management to protect sensitive information from malicious actors (Termly).
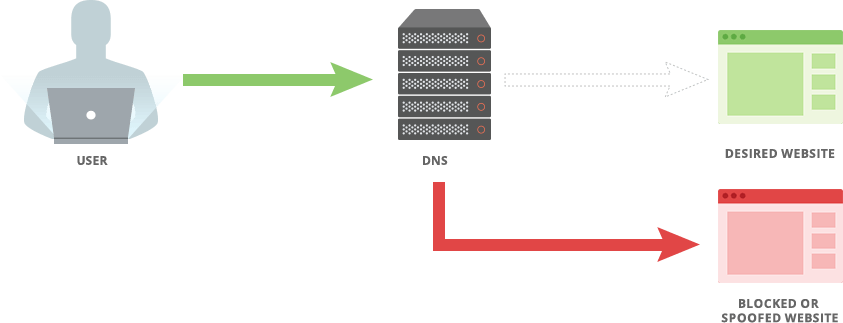
These recent hacks serve as a stark reminder of the evolving threat landscape and the necessity for continuous vigilance and advanced cybersecurity practices. As cybercriminals become more sophisticated, organizations must prioritize their cybersecurity strategies to safeguard against potential breaches and ensure the protection of critical data.
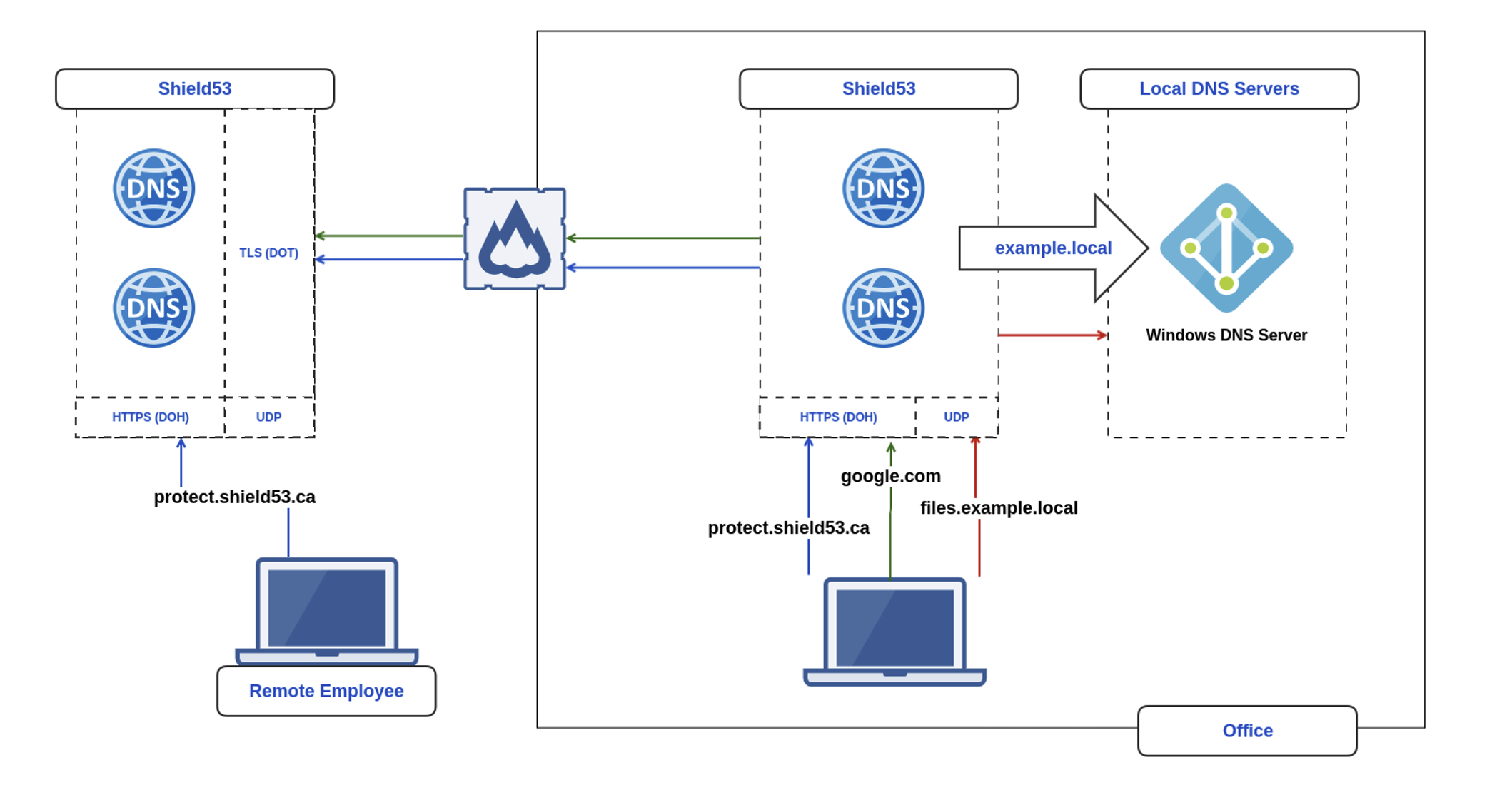
By partnering with Shield53, organizations can proactively defend against cyber threats, protect their critical data, and ensure resilience in the face of evolving cybersecurity challenges. Contact us today to learn more about how we can help secure your digital future.